My SimpliSafe doorbell lit its own fire this winter
...I'm just glad it was on the outside of the building, attached to non-flammable material :)
As part of my new studio/office buildout, I needed a 'smart' doorbell, so I could accept deliveries or see who rang, even if I was far from the door or recording.
I bought a SimpliSafe system for my location, and tied it into Home Assistant. It was easy to set up, the monthly cost was a fraction of what ADT wanted to charge, and yes, I know it's wireless-only communication can be tampered with. It's like a lock—it helps keep people honest, and is only one small part of a balanced security diet.
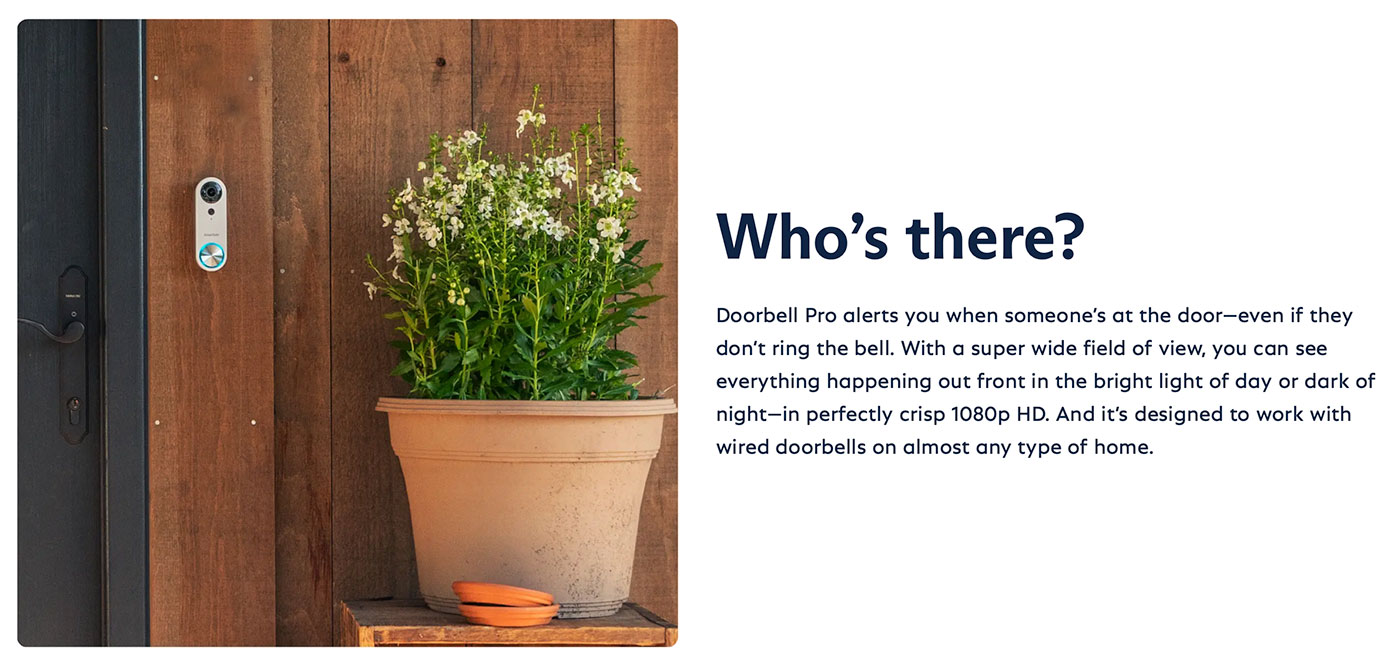
But I installed their Video Doorbell Pro a couple weeks ago, and setup was a breeze. Just get 24v doorbell wire to it, and bingo! You have a smart doorbell.

