Fixing Safari's 'can't establish a secure connection' when updating a self-signed certificate
I do a lot of local development, and since almost everything web-related is supposed to use SSL these days, and since I like to make local match production as closely as possible, I generate a lot of self-signed certificates using OpenSSL (usually using Ansible's openssl_* modules).
This presents a problem, though, since I use Safari. Every time I rebuild an environment using my automation, and generate a new certificate for a domain that's protected with HSTS, I end up getting this fun error page:
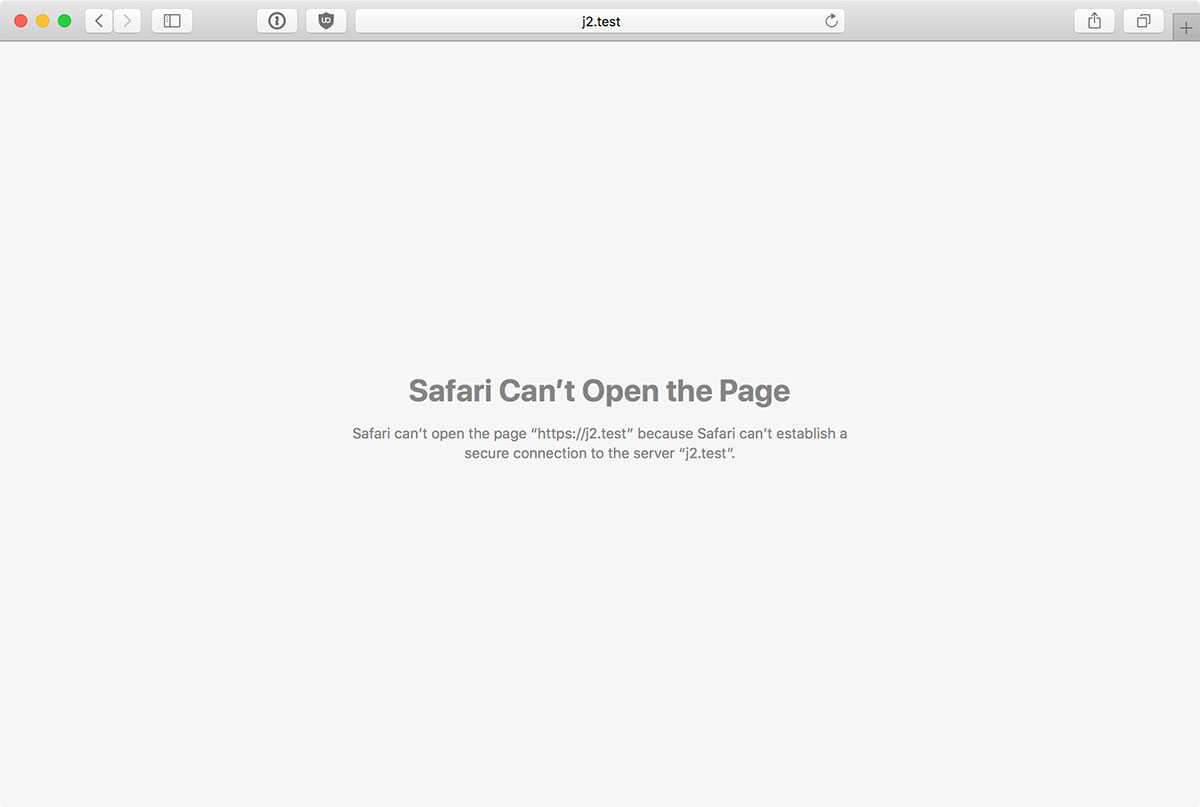
Safari Can't Open the Page – Safari can't open the page because Safari can't establish a secure connection to the server 'servername'.